LDAP Authentication method provides a feature-rich authentication method suitable for use with LDAP Directories, including Active Directory.
Key Features:
- Configuration setting to allow user creation on first successful login
- Optional synchronization of Users, Groups and Group Memberships
- Manual or Automatic synchronization of Users and Groups
- Authentication only setting
- Support for SSL and StartTLS
Enterprise Tester supports LDAP authentication and user synchronization.
Note that this functionality is for adding users only and ET does not currently support inactivating users or user deletion.
We recommend that you set up a group for ET users in AD and only import users from that group into ET. This helps to ensure that you only import ET users and that you don't exceed the number of named users for your license.
Enterprise Tester supports importing the following attributes into ET from LDAP:
1. First Name
2. Last Name
3. Email Address
4. Username
5. Phone Number.
The LDAP Configuration has 2 components:
- General configuration to your LDAP server; and
- Synchronization set up.
General LDAP Setup
AD Explorer
AD Explorer is an open source tool that can assist with navigation of the Active Directory structure. It is useful in helping to generate the correct filter syntax settings described below. You can download the tool from the Microsoft Windows Sysinternal site.
http://technet.microsoft.com/da-dk/sysinternals/bb963907.aspx
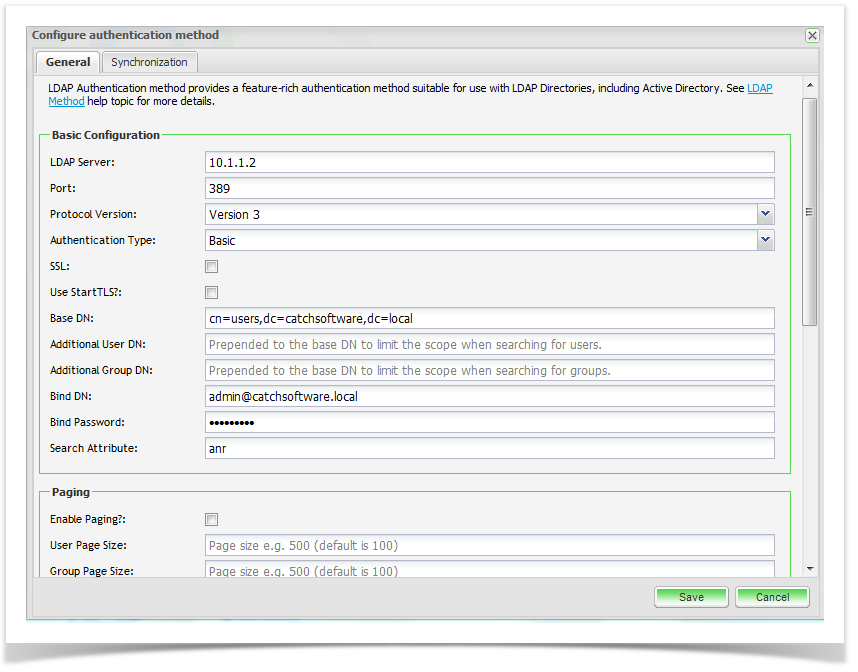
Basic Configuration
| Field | Description | Example |
|---|---|---|
| LDAP Server | Enter LDAP Serve Name or IP Address | 123.123.1.234 |
| Port | Port number associated with the LDAP Server | 389 |
| Protocol Version | Version of LDAP | Version 2 (required for some older OpenLDAP installations) or Version 3 (Active Directory and new LDAP Directory implementations) |
| Authentication Type | Authentication Protocol | Anonymous, Basic, Negotiate, NTLM, Digest, Sicily, Dpa, Msn, External or Kerberos |
| SSL | Encryption Protocol | Check if using SSL |
| StartTLS | Encryption Protocol | Check if using StartTLS |
| Base DN | Name of the root node in LDAP from which to search for users | cn=users,dc=example,dc=com |
| Additional User DN | Prepended to the Base DN to limit the scope when searching for users | |
| Additional Group DN | Prepended to the Base DN to limit the scope when searching for groups | |
| Bind DN | Bind DN is the user and the node in LDAP where the user can be found (this is the user Enterprise Tester will authenticate to the LDAP directory as - they must have sufficient rights to query the LDAP directory) | Either a value distinguished name such as "cn=user,cn=Users, dc=example,dc=com", an username@domain e.g. "joebloggs@mycompany.local" or left blank for anonymous authentication. |
| Bind Password | Password for the Bind DN user | Password, or left blank for anonymous authentication. |
| Search Attribute | The attribute in LDAP holding the login name | uid (common for OpenLDAP) or sAMAccountName (Active Directory) |
Paging
| Field | Description | Example |
|---|---|---|
| Enable Paging | When enabled, users will be returned in multiple pages rather than a single list. This is useful when you have a large number of users configured in LDAP, and where a non-paged request will fail because the query returns more than the allowable maximum - this should always be enabled for Active Directory. | True |
| User Page Size | Specify the number of users to return per page. The default value is 100. This value should ideally be configured to be the same as the maximum number of results which can be returned from a single query to ensure the least number of round trips when querying LDAP. | 1000 |
| Group Page Size | Specify the number of groups to return per page. The default value is 100. This value should ideally be configured to be the same as the maximum number of results which can be returned from a single query to ensure the least number of round trips when querying LDAP. | 500 |
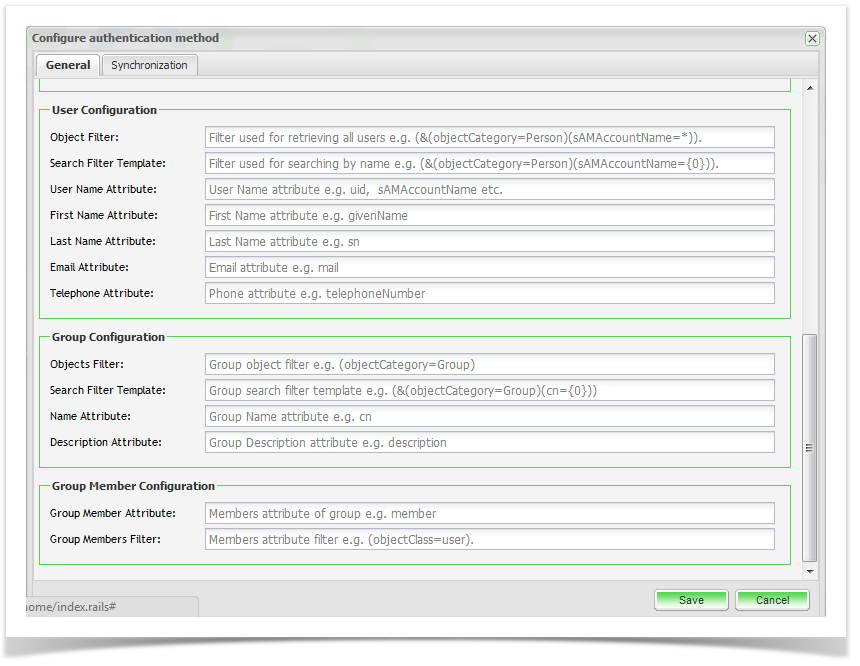
User Configuration
| Field | Description | Example |
|---|---|---|
| Object Filter | Filter user for retrieving all users | (&(objectCategory=Person)(sAMAccountName=*)) |
| Search Filter Template | Filter used for searching by name or partial name. | (&(objectCategory=Person)(sAMAccountName={0})) |
| User Name Attribute | User Name Attribute | uid (common for OpenLDAP) or sAMAccountName (Active Directory) |
| First Name Attribute | First Name Attribute | givenName |
| Last Name Attribute | Last Name Attribute | sn |
| Email Attribute | ||
| Telephone Attribute | Phone Attribute | telephoneNumber |
Group Configuration
| Field | Description | Example |
|---|---|---|
| Object Filter | Group Object Filter | (&(objectCategory=Group) |
| Search Filter Template | Group Search Filter Template | (&(objectCategory=Group)(cn={0})) |
| Name Attribute | Group Name Attribute | cn |
| Description Attribute | Group Description Attribute | description |
Group Member Configuration
| Field | Description | Example |
|---|---|---|
| Group Member Attribute | Members attribute of group | member |
| Group Members Filter | Members Attribute Filter | (objectClass=user) |
Once you have completed your configuration, select 'Save' at the bottom of the page.
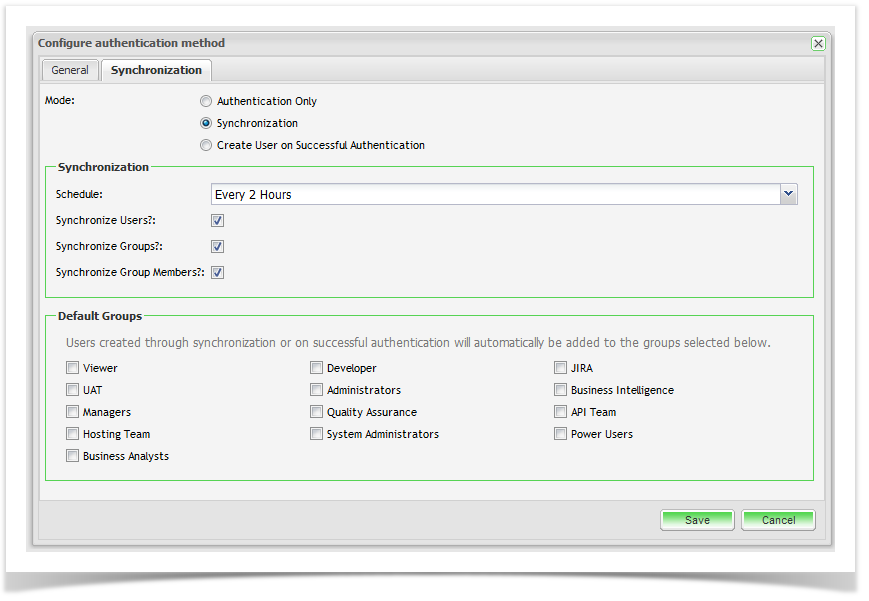
Synchronization
The synchronization section allows you to set up the synchronization mode, the frequency of synchronization and any default groups you wish to have new users added to when being synchronized with Enterprise Tester.
| Field | Description | Example |
|---|---|---|
| Mode | Select the type of integration you would like with LDAP |
|
| Schedule | Synchronization Frequency | Manual Synchronization, Every Hour, Every 2 Hours, Every 4 hours, Every 8 Hours and Every 24 Hours. |
| Synchronize Users | Select to synchronize Users from LDAP | Check to synchronize users |
| Synchronize Groups | Select to synchronize Groups from LDAP | Check to synchronize Groups |
| Synchronize Group Members | Select to synchronize Groups from LDAP | Check to synchronize Group Members for each user |
Default Groups
In the Default Group section you can configure all the groups you would like users to automatically be assigned to when they are created through synchronization with LDAP or through successful authentication on first login, this is in addition to any group memberships that user may have been automatically added if "Synchronize Group Members" is checked.
Unless you specify at least one default group (and assign that group view permissions for at least 1 project) any users created as a result of using the "Create User on Successful Authentication" option will be unable to use Enterprise Tester.