The machine source is a flexible method supporting authenticating users against the following three sources of user information:
- Active Directory
- Local Machine Users i.e. if the machine is not a member of a domain. This is also great for testing some authentication scenarios.
- AD LDS (Active Directory Lightweight Directory Services) - see here(http://technet.microsoft.com/en-us/library/cc755080%28WS.10%29.aspx) for more details.
The machine source only works with Active Directory, and not other LDAP directories. Because of this fact it's also a great deal easier to configure - if you wish to authenticate against the same domain as the server belongs to then no configuration is required what so ever!
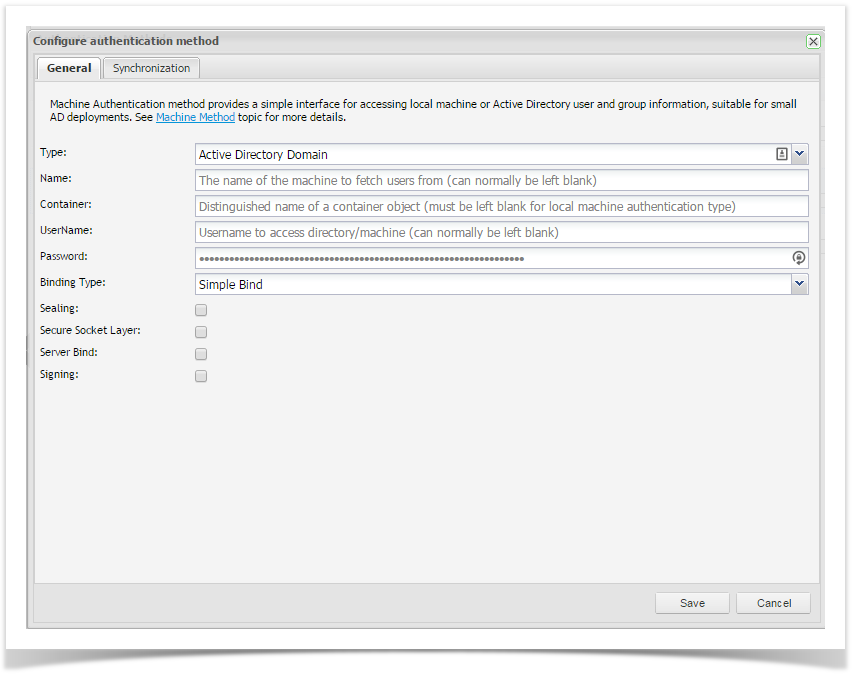
Machine Source Authentication method provides a simple interface for accessing the local machine or Active Directory user and group information. This is useful for small AD deployments.
| Field | Description | Example |
|---|---|---|
| Type | The type of users source, possible options are: Active Directory Domain, Active Directory LDS Store, or Local Machine | Local Machine |
| Name | Optional name of the server (either as the source of "local" users, or the active directory domain controller) | corp01 |
| Container | Use this only for Active Directory Domain or Active Directory LDS Store. This is the distinguished name of a container object for users/groups, this should be left blank for Local Machine users. | cn=users,dc=mycompany,dc=com |
| User Name | Username to access the directory/machine (can normally be left blank). | Administrator |
| Password | Password to access the directory/machine (can normally be left blank). | ******** |
| Binding Type | The authentication mode:
| Simple Bind |
| Sealing | The data is encrypted by using Kerberos. This flag can only be used with the Negotiate context option and is not available with the simple bind option. | Unchecked |
| Secure Socket Layer | The channel is encrypted by using the Secure Sockets Layer (SSL). Active Directory requires that the Certificate Services be installed to support SSL. | Unchecked |
| Sever Bind | Specify this flag when you use the domain context (Active Directory Domain type) if the application is binding to a specific server name. | Checked |
| Signing | The integrity of the data is verified. This flag can only be used with the Negotiate context option and is not available with the simple bind option. | Unchecked |
Synchronization
You can configure automatic synchronization of users, groups and group memberships from Active Directory.
| Field | Description | Example |
|---|---|---|
| Mode | Select the type of integration you would like with JIRA | 1. Authentication only –AD is used to authenticate users only 2. Synchronization – Users, Groups and Group Memberships are automatically created in Enterprise Tester 3. Create User on Successful Authentication – New users are automatically created on first login if they are successfully authenticated in LDAP |
| Schedule | Synchronization Frequency | Manual Synchronization, Every Hour, Every 2 Hours, Every 4 hours, Every 8 Hours, Every 24 Hours |
| Synchronize Users | Select to synchronize Users from LDAP | Check to synchronize users |
| Synchronize Groups | Select to synchronize Groups from LDAP | Check to synchronize Groups |
| Synchronize Group Members | Select to synchronize Groups from LDAP | Check to synchronize Group Members |